Exploiting human flaws to get access to personal information and secure systems is known as “social engineering attack” Instead of hacking computer systems to get access to a target’s account, social engineering depends on influencing people. Social engineering attacks are carried out via a series of phases. To carry out the assault, a perpetrator first examines the target victim to obtain relevant background information, such as potential avenues of entry and weak security mechanisms. The attacker then attempts to acquire the victim’s confidence and gives stimulus for later acts that violate security protocols, such as disclosing sensitive information or providing access to key resources.
Hackers also try to take advantage of a user’s ignorance. Because of the pace at which technology advances, many customers and employees are unaware of hazards such as drive-by downloads. Users may also be unaware of the full value of their personal information, such as their phone number. In this article, we will try to shed some light on the definition of social engineering and its types or techniques, which are most commonly used.
Recommended: https://offsecpath.com/top-5-books-to-learn-ethical-hacking-that-you-can-buy-today/
The Methodology: Social Engineering Attacks
The majority of social engineering attacks rely on direct communication between the attacker and the victim. Rather than utilizing brute force tactics to penetrate your data, the attacker will try to persuade the user to compromise themselves. The assault cycle provides these crooks with a repeatable method of deception. The following are the steps in a typical social engineering assault cycle:
- Gather background information on yourself or a broader organization to which you belong.
- Infiltrate through forming a connection or commencing a contact, which begins with the establishment of trust.
- To escalate the assault, exploit the target after trust and a weakness have been developed.
- Once the user has completed the specified activity, disengage.

Social Engineering Attacks Techniques
Social engineering assaults occur in a variety of shapes and sizes, and they may be carried out anyplace there is human interaction. These attacks have connection with almost every sort of cybersecurity attack. The traditional email and virus frauds, for example, have social connotations. Social engineering assaults on mobile devices, as well as desktop ones, can have a digital influence on you. You may, however, be confronted with a threat in person. These assaults may be layered on top of one another to form a hoax.
The following are some of the most commonly used techniques employed by social engineering attackers:
Phishing
In a phishing attack, a perpetrator sends a message to a victim via email, social media, instant messaging apps, or SMS in order to fool them into providing personal information or clicking a link to a malicious website.
By sparking curiosity, pleading for assistance, or employing other emotional triggers, phishing communications attract a victim’s attention and prompt them to take action. They frequently mimic an organization’s identity using logos, photos, or writing styles to make it appear as though the communication came from a work colleague, the victim’s bank, or another legitimate channel. The majority of phishing communications employ a feeling of urgency to make the target believe that if they don’t swiftly hand over sensitive information, bad things will happen.
Variations of Phishing Attacks

- Email phishing: This is how classic phishing works, when the email recipient is enticed to reply or follow up in another way. Malicious links or attachments might be present in the email.
- Voice phishing (vishing): a phone call, which might be from a live person or an automated message system. The assailant calls the victim and asks for private information or persuades them to do something.
- SMS phishing (smishing): communications sent via SMS or mobile apps that might ask the victim directly for personal information or include dangerous links.
- Angler phishing: an assaulter’s attempt to pretend to be a reputable company’s customer care department or social media account. Through the use of private messages, the attacker is able to intercept communications with brands and utilize them to launch phishing attacks.
- Search engine phishing: an effort by attackers to rank phony websites first in search results This might be accomplished through paid advertising, legal search engine optimization strategies, or “black hat” methods.
- In-session phishing: a client session during which an attacker tries to obstruct regular online browsing. For instance, the attacker may send the user to a malicious website or insert a phony login prompt.
- Spear phishing or “whaling”: employing any of the aforementioned methods, targeted phishing to a specific person or department based on earlier reconnaissance
Scareware

This kind of phishing technique bombards victims with bogus threats and misleading alarms. Users are tricked into believing their computer is infected with malware, which leads them to install software that either serves only to profit the perpetrator or is malware in and of itself. Other names for scareware include fraud ware, deception software, and rogue scanning software.
The legitimate-appearing popup ads that show in your browser as you browse the internet and contain language such as “Your computer may be infected with hazardous spyware applications” are a frequent type of scareware. It will either send you to a malicious website where your computer becomes infected or offer to install the program (frequently tainted with malware) for you. Additionally, spam emails that issue false alerts or urge recipients to purchase useless or hazardous services are used to spread scareware.
It’s goal is to mislead users into buying fraudulent software or further infecting their machine. These display pop-up security notifications to consumers that resemble alerts from legitimate antivirus providers. These messages typically suggest that files are contaminated or the device is in danger. Various variations include RAM limit alerts, unused application cleanup services, and other hardware- or software-based upgrades.
pRETEXTING
Pretexting is a form of social engineering attack in which the attacker fabricates a situation in which the victim feels pressured to comply. In order to get the victim to comply with their instructions, the attacker frequently assumes the identity of someone in a position of authority. A bad actor may pose as a police officer, a corporate executive, an auditor, an investigator, or any other identity they feel will assist them in obtaining the information they need during this sort of social engineering assault.
Baiting As A Social Engineering Attack

Attackers lure victims by offering something they think would be helpful. This might come through a purported software update that is actually a malicious file, a USB token that has been infected and is labeled as containing important data, or other means. A quid pro quo assault is similar to baiting, except instead of giving the victim something of value, the attackers promise to do something for their own advantage in exchange for the victim doing an action. For instance, a hacker may claim to be calling back on a technical support request while dialing random corporate lines. They pretend to assist someone who truly needs assistance but provide them instructions on how to compromise their machine when they discover someone who actually needs support.
Physical breaches and tailgating

A crude kind of social engineering attack called tailgating is utilized to physically enter an unapproved site. Tailgating is the practice of moving in close proximity to an authorized user without the authorized person noticing. Before the door is fully closed and latched, an assailant may sneak up behind a victim and ram their foot or another item against the door. Unauthorized people follow authorized people to secure locations using the social engineering tactic known as “tailing,” which is a physical breach. Tailgating is a straightforward social engineering-based technique that gets around ostensibly reliable security measures. Employees could keep the door open for a sneaky attacker who follows them closely, enabling them to get past authentication safeguards.
Disgruntled former workers, criminals, and saboteurs who want to steal from or destroy a corporation are examples of potential tailgaters. Once inside guarded places, they have the ability to harm property, disrupt operations, steal data, and launch subsequent assaults using the knowledge they have gained.
Watering hole
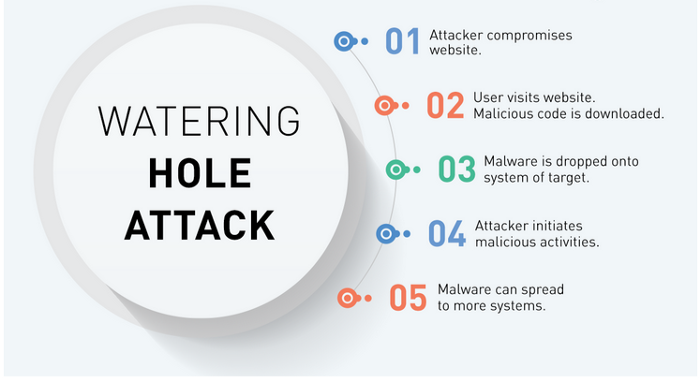
A genuine website that is often frequented by the targets of the assault is used to launch or download malicious malware in a watering hole attack. A financial sector news website, for instance, may be compromised by attackers who are aware that visitors to the site are likely to be people who work in finance and are thus an appealing target. A backdoor trojan that the hacked site generally installs enables the attacker to access and remotely manipulate the victim’s device.
According to the warnings on banks from 2017, watering hole attacks are typically carried out by competent attackers who have found a zero-day flaw and/or are searching for a specific “kind” of customer or workers of a particular organization who utilize a specific HR resource or tool. To protect the value of the exploit they found, they may postpone the real attack for months. Watering hole attacks may occasionally target the target audience’s susceptible software directly, as opposed to a website they visit.
Suggested Read:https://offsecpath.com/five-phases-of-ethical-hacking/
